
What Is DORA Legislation? A Guide For Banks, Fintechs & Financial Institutions
 11:50 21 Sep 2023
11:50 21 Sep 2023 The EU’s Digital Operational Resilience Act comes into force in just two years. Cybersecurity experts Duncan McDonald, Global Head of Compliance Services & Wayne Scott, Regulatory Compliance Lead, from The NCC Group explain how to prepare for DORA compliance and why the new legislation will enhance cyber resilience across the financial sector and its supply chain.

If you haven’t started preparing for a game-changing piece of European legislation called the Digital Operational Resilience Act (DORA) – it’s time to take action immediately.
Just like GDPR before it, DORA applies only to EU member states but will likely impact companies around the world. In fact, its scope dwarfs the now-famous data protection legislation. Financial services organisations of all sizes and in every sector will have to comply with DORA or face:
- Financial penalties.
- Compensation for damages (to customers or third parties).
- Public reprimands (from ESAs) and reputational damage.
- Withdrawal of authorisation.
The new legislation has unprecedented and far-reaching requirements. With GDPR, firms had to lock down personal datasets, identify the data they held, establish exactly who could access it and then put appropriate controls in place to protect that information. With DORA, financial services institutions will have to secure their entire business and ensure their suppliers are also compliant.
DORA came into force on 27th Dec 2022 and organisations have until 17th Jan 2025 to become compliant. This is no small task, which is why NCC Group is calling on all players in the global financial services ecosystem to make DORA compliance a priority.
We can see what’s coming down the line. Banks, fintechs, all other financial institutions and their supply chains must take the necessary steps to comply or risk paying a very heavy price both financially and reputationally.
What Is The Digital Operational Resilience Act (DORA)?
DORA is designed to “make sure the financial sector in Europe is able to stay resilient through a severe operational disruption”, the Council of the EU wrote in a statement announcing DORA in 2022.
“We live in uncertain times,” Zbyněk Stanjura, Minister of Finance of Czechia, said. “Banks and other companies which provide financial services in Europe already have plans in place for their IT security, but we need to go one step further. Thanks to the harmonised legal requirements which we adopted today, our financial sector will be better able to continue to function at all times.”
The legislation sets out tough new requirements for the security of networks communicating any service deterioration, concentration risk and information systems of organisations operating in the financial sector – as well as the third parties which provide Information Communication Technologies (ICT) services to these institutions. It also reaches into areas like Operational Technology and the resilience associated with it. This new regulatory framework covers digital operational resistance and is intended to ensure firms can “withstand, respond to and recover from all types of ICT-related disruptions and threats”.
Regulators will have the power to impose fines of up to 1% of daily turnover for every single day that a company is deemed to be non-compliant, which will be calculated by analysing the previous year’s revenue.
DORA won’t apply directly to the UK financial services sector, due to Brexit, although many financial firms operate in Europe so will have to comply with the Act. The rules are also part of a global regulatory push towards operational resilience. The Bank of England, Prudential Regulation Authority (PRA) and Financial Conduct Authority (FCA) have already completed much of the work on operational resilience guidelines. The PRA SS2/21 regulation imposes requirements on the financial institutions as well as those within the wider financial market infrastructure (FMI).
The types of financial institutions DORA regulates include:
- Credit and payment institutions
- Electronic money institutions
- Investment and insurance firms
- Crypto-asset service providers
- Alternative investment fund managers
- Credit rating agencies
- Audit firms
- Crowdfunding service providers
- Stock exchanges and clearing houses
The regulation recognises that firms are increasingly vulnerable to threats in their supply chains, so DORA also applies to providers of critical ICT third-party services (CTPPs) including cloud, software, data analytics and data centre providers.
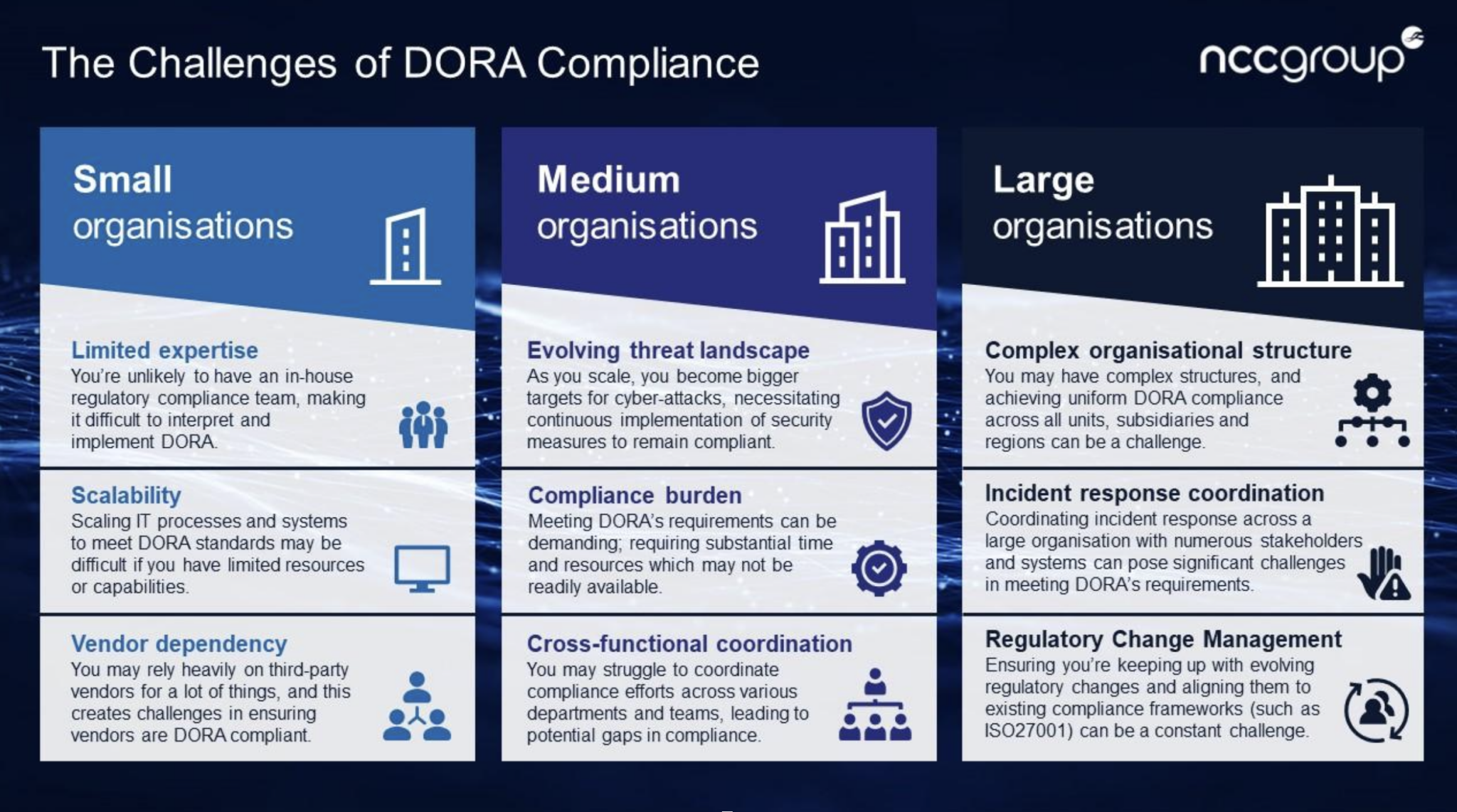
What Are The Challenges of DORA Compliance?
It is likely that mid-tier businesses such as Software-as-a-Service providers will find compliance to be the most challenging. Large providers such the big, global tech providers have the resources available to quickly implement DORA requirements, particularly because they already have most certifications in place already. Similarly, Tier One banks and the very biggest fintechs will probably be the most aware of what they need to do in order to be DORA compliant. compliance. But supplier failure and deterioration should not go ignored whether you’re a large or small organisation. And achieving compliance can be an easier thing to say than done!
Also, DORA directly regulates the systemic suppliers. This will be the first time, outside of the likes of any communications watchdog, that these systemic suppliers will be under direct scrutiny. This is a level of regulation never seen before and will involve substantial change when it comes to supplier failure, service deterioration and concentration risk. These suppliers will face three possible problems;
- Their own resilience.
- The resilience of their supply chain.
- The resilience of anything they host that is used by the financial institution.
There will be a ripple effect as larger organisations start to demand that their suppliers prove their compliance. Every smaller organisation that deals with large institutions will have to comply or risk losing contracts. There may be changes to contracts and the liability terms in those agreements as financial institutions, and their suppliers, take ownership of the compliance requirements imposed on them by the DORA legislation. Any known attack or cyber incident will need to be reported to the regulator. They may make the decision to push the financial institution to move away should it present a risk to the overall stability of the market. Additionally, any service that is repeatedly found unable or unwilling to accommodate the necessary fixes to become compliant would potentially be pulled under direct regulation of the ESAs.
Any sale of products or services due to be completed between now and the deadline will need to be revisited to ensure compliance. This will also affect pre-existing contracts because ICT providers will suddenly have to work out how to ensure the services they deliver are resilient.
Whilst DORA brings with it specific asks for financial institutions and their third-party suppliers, the concept of ensuring that business-critical operations are secure, resilient and can withstand disruption is not a new one. There should already be a level of protection and business continuity measures in place for existing suppliers and their contracts which will require a review and further action.

How To Prepare For DORA Compliance
The first step is determining whether your organisation and your critical ICT third-party providers fall under DORA’s remit (or the UK equivalent). A cyber security review will help to identify strengths and weaknesses and provide a roadmap to improvement. Here are some of the steps organisations should follow when preparing for DORA.
Create a compliance framework: DORA requires a compliance model to be in place from the start. This should include policies, procedures, protocols, and tools needed to protect your organisation’s assets.
Manage cyber and non-cyber risks: DORA places a greater responsibility on financial services firms to classify, report and respond to threats and incidents. Major incidents must be reported to a national regulator within strict deadlines, which will be standardised across member states.
Test for threats and vulnerabilities: Companies must put measures in place for regular testing including vulnerability scans, network assessments, and penetration assessments. Testing processes should be regularly reviewed and updated to ensure continued compliance.
Manage third-party risk: To ensure DORA compliance, financial institutions need to understand the risk outsourced providers pose to their own security as well as the entire ecosystem. They will have to increase oversight of third-party providers, to ensure contracts are DORA-compliant and guarantee they are following suitable risk management procedures. If a business finds that a supplier is non-compliant, it must stop using its services.
Assign ownership: Manage supplier failure, service deterioration and concentration risk at the most senior level. The sooner that this is actioned, the sooner that policy can be changed, processes can be amended, and risks can be mitigated. The mistake is often made to include supplier failure risk within the wider remit of cyber security, however as cyber security is not the main cause of supplier failure this means that the risk can go unmanaged with damaging results.
Share information: The DORA legislation encourage financial services organisations and third-party providers to share information on cyber threat intelligence, such as security alerts, tactics, procedures, and threat detection. In the UK the NCSC has a cyber information sharing platform called CiSP as well as the financial sector cyber collaboration centre (FSCCC). In the EU, the Joint Cyber Unit (JCU) will perform a similar role and help firms to counter large-scale cyber attacks
Organisations have just two years to become compliant. Preparation cannot be postponed. DORA is one of the biggest regulatory changes the financial services sector has ever seen, so now is the time to start your countdown to compliance and adopt a new approach to resilience.
Get in touch with NCC Group and discuss how to prepare your business for DORA: https://www.nccgroup.com/uk/campaign/critical-infrastructure-regulatory-compliance/critical-infrastructure-assessment-request-form/



 " alt="">
" alt="">

 " alt="">
" alt="">
 " alt="">
" alt="">
 " alt="">
" alt="">
 " alt="">
" alt="">
 " alt="">
" alt="">
 " alt="">
" alt="">
 " alt="">
" alt="">
 " alt="">
" alt="">